La informática forense es una de las disciplinas que mas me apasiona, y todavía no he hablado en el blog sobre esta rama de la seguridad informática como se merece; así que hoy vamos a ver como recuperar archivos borrados con la técnica de file carving utilizando Foremost.
Cierto es que existen muchas mas aplicaciones para llevar a cabo esta tarea, pero esta herramienta y Scalpel son las que mas me gustan, y las que he utilizado cuando alguna vez por descuido he borrado lo que no debía; las dos me han ayudado a bajar el porcentaje de probabilidad de sufrir alopecia, o infartos a una edad temprana.
Para la siguiente práctica, vamos a necesitar un pendrive, y algunos archivos en diferentes formatos.
Lo que vamos a hacer con este pendrive, se haría de igual forma en cualquier soporte de almacenamiento distinto; la única diferencia es que para realizarlo en discos duros, tendremos que abrir nuestro PC de sobremesa; contar con un puerto eSata; o disponer de una controladora USB para IDE/PATA/SATA.
Yo prefiero la opción de la controladora, ya que nos permite trabajar con todo tipo de discos duros; ya sean nuevos o viejos, de 2,5″ o de 3,5″, es bastante económica y a este modelo en concreto se le pueden conectar hasta dos discos a la vez.
Archivos
Como antes comentaba, necesitaremos algunos archivos a recuperar, yo he copiado los míos en un pendrive.
Paquetes necesarios
Para llevar a cabo esta práctica necesitamos Foremost, así que vamos a ver que paquete debemos instalar para disponer de este software, afortunadamente está disponible en los repositorios oficiales, así que solo tendremos que utilizar la herramienta apt.
usuario@maquina:~$sudo apt-get install foremost
Borrando el contenido
Primero vamos a borrar nuestros archivos, y para ello vamos a utilizar el comando rm con el argumento -r para hacer borrado recursivo y -f para forzar el borrado; finalmente como objetivo seleccionaremos * es decir, le indicaremos que borre todos los archivos dentro de nuestro pendrive o disco duro.
#Nos movemos al directorio donde se ha montado nuestro soporte de almacenamiento.
usuario@maquina:~$ cd /media/ruta-del-disco
#Borramos todo el contenido.
usuario@maquina:~$ sudo rm -rf *
#Listamos el contenido para comprobar que ya no queda nada.
usuario@maquina:~$ ls
usuario@maquina:~$Que es Foremost, y como funciona internamente
Foremost Forensic Tool es una herramienta de recuperación de archivos desarrollada inicialmente por el departamento de investigaciones especiales de las fuerzas aéreas del ejército de los Estados Unidos de América.
Debemos tener en cuenta que cuando borramos un archivo, lo único que hacemos es ocultarlo a la vista del usuario, marcando como libres los cluster ocupados por el; a la espera de que se requiera ese espacio, para entonces sobreescribirlo.
Entender su forma de recuperar archivos es bastante sencillo, ya que lo que hace es recorrer el disco tratando de reconocer los archivos por la estructura de los headers y los footers en formato hexadecimal de cada tipo de archivo, ya que estos son genéricos.
Configurar Foremost a nuestro gusto
Para configurar Foremost de una forma personalizada, solo tenemos que editar su archivo de configuración /etc/foremost.conf y descomentar los formatos de archivos que queremos buscar; hacer esto no es necesario, ya que dispone de configuraciones por defecto para todos los formatos, pero podemos cambiar el header y el footer en hexadecimal si lo deseamos, e incluso añadir tipos de archivo distintos.
usuario@maquina:~$sudo nano /etc/foremost.conf
A continuación podéis ver una muestra de parte del contenido del fichero de configuración, en concreto las líneas que hacen referencia a los formatos que vamos a recuperar; si quisiéramos cambiar algún parámetro solo deberíamos descomentar la línea asociada a la extensión deseada, para finalmente cambiar esos valores.
#---------------------------------------------------------------------
# GIF and JPG files (very common)
# (NOTE THESE FORMATS HAVE BUILTIN EXTRACTION FUNCTION)
# gif y 155000000 \x47\x49\x46\x38\x37\x61 \x00\x3b
# gif y 155000000 \x47\x49\x46\x38\x39\x61 \x00\x00\x3b
# jpg y 20000000 \xff\xd8\xff\xe0\x00\x10 \xff\xd9
# jpg y 20000000 \xff\xd8\xff\xe1 \xff\xd9
# jpg y 20000000 \xff\xd8 \xff\xd9
#
# PNG (used in web pages)
# (NOTE THIS FORMAT HAS A BUILTIN EXTRACTION FUNCTION)
# png y 200000 \x50\x4e\x47? \xff\xfc\xfd\xfe
#
#---------------------------------------------------------------------
# ADOBE PDF (NOTE THIS FORMAT HAS A BUILTIN EXTRACTION FUNCTION)
#---------------------------------------------------------------------
#
# pdf y 5000000 %PDF- %EOF
#
#---------------------------------------------------------------------
# (NOTE THIS FORMAT HAS BUILTIN EXTRACTION FUNCTION)
# zip y 10000000 PK\x03\x04 \x3c\xac
#---------------------------------------------------------------------Recuperar nuestros archivos con Foremost
Recuperar archivos con Foremost es realmente sencillo, solo debemos ejecutarlo con las opciones deseadas; a continuación explicaré las que yo he escogido.
– v activa el modo verbose, para que foremost muestre mas información del proceso mientras lo está llevando a cabo.
– t indica el tipo de archivo a recuperar.
– T añade la fecha al nombre del directorio donde se recuperarán los datos, así no deberemos cambiar el nombre del directorio cada vez que ejecutemos foremost.
– i indica el nombre de la partición de donde queremos recuperar los archivos.
– o indica el directorio donde queremos que foremost guarde los archivos recuperados.
Es muy recomendable ojear el manual para despejar cualquier duda al respecto.
usuario@maquina:~$man foremost
Foremost soporta muchos formatos distintos, y para no repetir la operación uno a uno le vamos a indicar que recupere todos los formatos disponibles con el argumento all para la opción -t; es posible que así tarde mas, pero nosotros vamos a dejarlo trabajando, e iremos a tomarnos un café o a realizar otras tareas durante ese periodo de tiempo.
usuario@maquina:~$ sudo foremost -v -T -t all -i /dev/sdb1 -o /home/usuario/Escritorio/recuperado
[sudo] password for usuario:
Foremost version 1.5.7 by Jesse Kornblum, Kris Kendall, and Nick Mikus
Audit File
Foremost started at Sat Dec 27 12:13:03 2014
Invocation: foremost -v -T -t all /dev/sdb1 -o /home/usuario/Escritorio/recuperado
Output directory: /home/usuario/Escritorio/recuperado
Configuration file: /etc/foremost.conf
Processing: /dev/sdb1
|------------------------------------------------------------------|
File: /dev/sdb1
Start: Sat Dec 27 12:13:03 2014
Length: 7 GB (8010072064 bytes)
Num Name (bs=512) Size File Offset Comment
*0: 00266344.png 74 KB 136368128 (297 x 222)
1: 00267240.png 2 MB 136826880 (2176 x 1915)
2: 00275456.png 22 KB 141033603 (181 x 256)
3: 00275520.png 21 KB 141066371 (181 x 256)
4: 00275664.png 87 KB 141139968 (1157 x 654)
5: 00275840.png 297 KB 141230080 (1023 x 635)
6: 00276480.png 255 KB 141557760 (1021 x 588)
7: 00276992.png 21 KB 141819904 (912 x 553)
8: 00277040.png 106 KB 141844480 (1308 x 701)
9: 00277256.png 10 KB 141955072 (797 x 114)
10: 00277280.png 49 KB 141967360 (519 x 485)
11: 00285584.png 21 KB 146219139 (181 x 256)
*********************************************************************
*********************************************************************
2869: 02437564.dll 51 KB 1248032768 10/20/2010 13:24:41
2870: 02437679.dll 79 KB 1248091648 10/20/2010 13:24:50
2871: 02437850.dll 68 KB 1248179200 10/20/2010 13:24:41
2872: 02438005.dll 358 KB 1248258560 02/24/2011 04:00:44
2873: 02438756.dll 51 KB 1248643072 10/20/2010 13:24:41
2874: 02438872.dll 79 KB 1248702464 10/20/2010 13:24:50
2875: 02439043.dll 68 KB 1248790016 10/20/2010 13:24:41
2876: 02439199.dll 358 KB 1248869888 02/24/2011 04:00:44
|********************************************************************|
Finish: Sat Dec 27 13:09:06 2014
2974 FILES EXTRACTED
gif:= 347
jpg:= 483
png:= 922
avi:= 119
pdf:= 278
zip:= 2
exe:= 132
dll:= 691
------------------------------------------------------------------
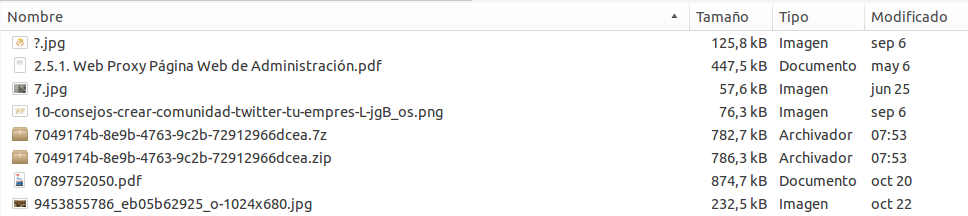
La recuperación ha tardado poco menos de una hora, aunque esto variará dependiendo del tamaño de la partición, la cantidad de formatos a recuperar, y del equipo con el que realizamos la tarea; he acortado la lista de archivos, ya que han sido más de 2900 archivos recuperados en diferentes formatos, y con fechas que datan desde 1998 hasta ahora.
Quiero recalcar que el pendrive lo compré en 2013, así que los demás datos deben ser un regalo navideño del Sr. Kingston; pero yo sin ánimo de ser desagradecido, voy a borrarlos.
Una vez que la aplicación termine su tarea, nos dirigiremos al directorio que hemos llamado “recuperado“, y en su interior encontraremos una carpeta asociada a cada formato; dentro de ellas están los archivos que se han logrado recuperar, pero antes debemos cambiar los permisos para poder acceder a estos directorios.
usuario@maquina:~$sudo chown usuario -R /home/usuario/Escritorio/recuperado_DíaSemana_Mes_DíaMes_Hora_Minuto_Segundo_Año
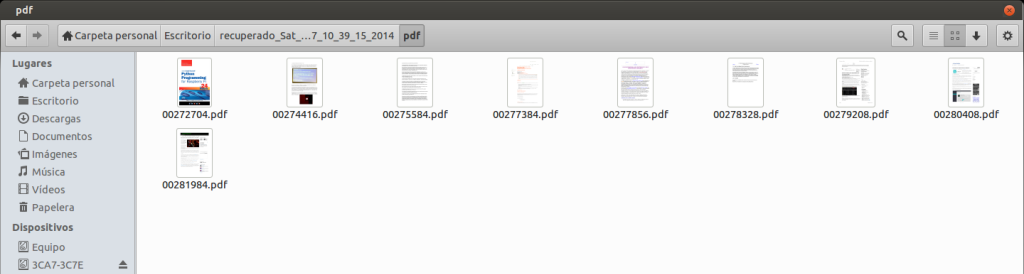
Ahora ya podemos acceder al directorio que contiene nuestros archivos; todos y cada uno de ellos han sido recuperados satisfactoriamente, veamos como ejemplo el interior de la carpeta que contiene los archivos PDF recuperados.
Si te ha gustado puedes seguirme en Twitter, Facebook, Google+, Linkedin, o compartirlo con los botones ubicados debajo de esta publicación, si tienes cualquier pregunta o sugerencia no dudes en comentar.







![BCN Raspberry JAM – Sistemas de videovigilancia libres [14/11/15]](http://www.peatonet.com/wp/wp-content/uploads/2015/11/Captura-de-pantalla-de-2015-11-18-113251-150x150.png)





![Criptografía – Píldoras formativas del proyecto Thoth: Pildoras 7 y 8 [Criptored]](http://www.peatonet.com/wp/wp-content/plugins/related-posts-by-zemanta/static/thumbs/17.jpg)





Buenas tardes, desde Venezuela ¿ Como puedo recuperar un pen drive? ¿ sabe de alguna aplicación?